A security expert and hacker receives $250,000 from Google out of the blue. He doesn't want to keep the money but has a hard time returning it.
Sam Curry is a hacker and security researcher who occasionally collects rewards for found software bugs. However, he does not know why he received $250,000 (about a quarter of a million euros) from Google last month and therefore wants the Internet giant to take the money back. But that turns out to be not so easy.
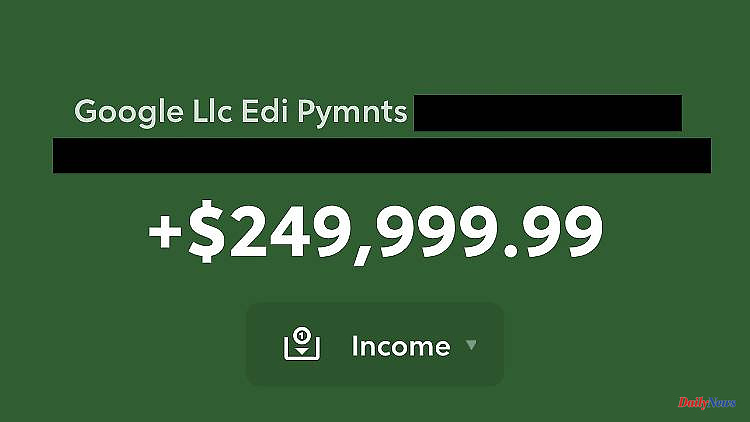
It's been over three weeks since Google accidentally sent him $249,999, he tweeted a week ago, along with a screenshot of the transaction. He contacted support and his request was confirmed by a ticket. But he's still waiting for an answer. "Is there any way to get in touch with @Google?" he asked, adding, "It's okay if you don't want it back."
Curry told radio station NPR that as a security engineer, he sometimes runs bug bounty hunts for companies like Google. It pays people to help companies and other organizations find vulnerabilities in their software. However, the transfer has nothing to do with a successful hunt for Google, apparently he received the money by mistake.
Curry said he is waiting for the $250,000 to be recovered. However, if Google takes too long, it may have to transfer the sum to another account in order not to have to pay tax for the high amount.
Meanwhile, a Google spokesman has confirmed to NPR that the transfer was a mistake. Due to a "human error," the team sent the money to the wrong recipient, the statement said. "We appreciate that the affected partner was quick to let us know and we are working to correct this."
It is not known whether Curry has lost the quarter million again. He still had the money in his account last Thursday, he told NPR. He has also not yet reported on Twitter that Google has become active.