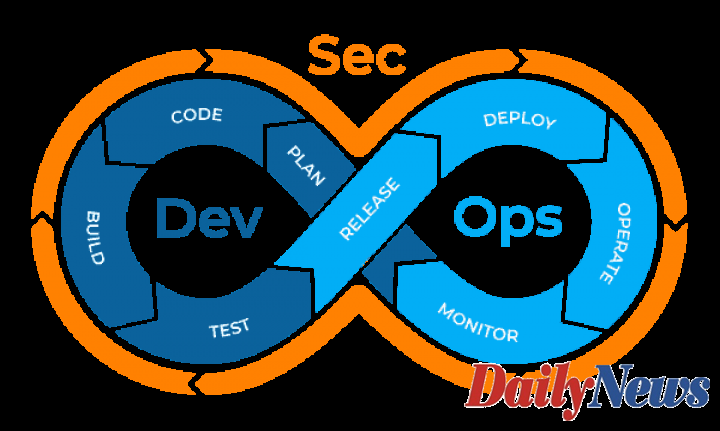
Although development, security, and operations are integral to software development, the processes involve a change in how they are used. Are you planning to implement DevSecOps or Security DevOps for your business operations? Keeping a few essential points in mind will ensure that you implement them the right way.
What Do You Understand By Security DevOps?
In simple terms, this process refers to integrating security checks at every step of the development process. With this process, security is not added on at the last step as an afterthought. Rather, companies ensure a robust security system for each step of the process.
With Security DevOps, teams work together to ensure that the final product meets our quality requirements and standard. Collaboration of different teams is crucial for this process to be effective. Successful use of this process can help you build a secure app, not just in functions but also in its environment. Using end to end devops consulting services can help you build a secure app, not just in functions but also in its environment.
What Are Essentials for Successful Security DevOps?
Does implementing security checks in your continuous integration, delivery, and deployment pipeline sound complicated? Well, it is.
Understanding how it implements this process the right way can take some time. However, when it’s done the right way, you will see a great benefit for your company.
Implement Pre-commit Checks
Pre-commit checks are performed before developers commit codes into the final program. With these checks, it is easier to catch security issues early on and change them before integrating them into the software. Though it may seem time-consuming at first, a pre-commit check helps in saving time in the long run.
Using Automated Testing
With DevSecOps, automation is crucial. When tests are automated, it ensures uniform results that can be compared easily. It is much easier to gauge security risk at every step and for the overall software when you have comparable results.
Automated Security Updates and Notifications
When analyzing your software for vulnerabilities, some may come up more often than others. Hence, it is best to automate the security checking process for tests of known vulnerabilities.
When assessing vulnerabilities, development and security teams must work together to find common vulnerabilities. Once common or frequent vulnerabilities are assessed, it is easier to automate testing that checks for these known vulnerabilities.
Performing Timely Checks
While it may sound easy in theory, implementing security checks at every stage is more complicated than it seems. It is not just pre-commit checks but includes commit-time checks, build-time checks, test-time checks, and deploy-time checks.
Although it may seem repetitive, performing checks at every point ensures that no vulnerabilities are missed.
Data Encryption
Encrypting data is also crucial for security. Teams must ensure encryption of data between the software and the service. Using data encryption, your team can help prevent unauthorized access to personal data.
Data Compliance
For every business, compliance is crucial. System and service configuration ensures that your software adheres to all compliance guidelines. Without checking for compliance issues, deployment is not possible.
Hence, Security DevOps helps build a sound security system and maintains compliance across different software. Manual errors can easily be eliminated using automated compliance processes.
Input Validation Tests
Creating security checks for input is essential as well. Verification, validation, and authorization processes are important for the end-user. For the final product to be effective, features such as password validation and authorization are essential.
Implementing Principle of Least Privileges
Many companies find it beneficial to employ the Principle of Least Privileges. This not only eliminates manual error but enhances security as well. With this principle, any unauthorized changes to the code are prevented, which can be useful if security checks take a little longer than usual.
When implementing the DevSecOps process, it is crucial to keep in mind that the principles of this process are only a foundation. Each guideline should be adapted to your business requirements and needs.
For this process to work, Security DevOps teams must work collaboratively. While most companies may believe in creating a bottleneck security team, this approach is not effective.
With a bottleneck, teams cannot communicate effectively, which can hinder the development and deployment process. Experts suggest that collaborative effort is crucial to help keep things running smoothly.
DevSecOps may not be new, but implementing its integrated approach is. The process has evolved rapidly over the last few years. What was acceptable a few years back may not be used in the current approach.
To guarantee a successful implementation, ensure that you stay up to date on recent developments within the Dev, Sec, and Ops world to understand how you can use it for your business.
Date Of Update: 24 September 2021, 18:30