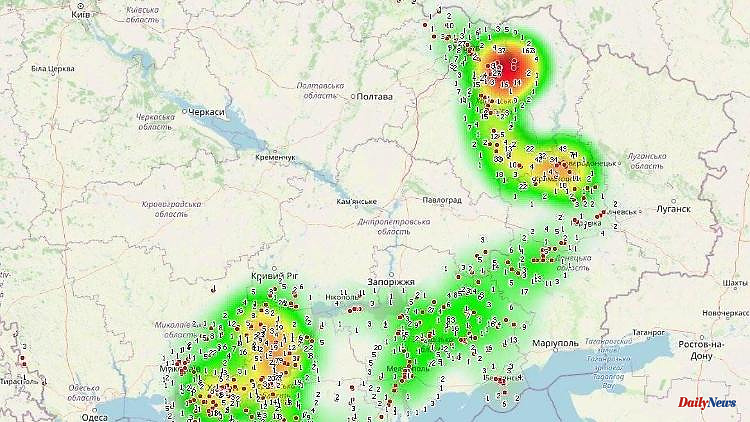
A map section is being discussed on the Internet, which apparently shows the Russian troop concentrations in Ukraine based on smartphone localization. It is unknown where the data came from. What is certain, however, is that cell phone tracking plays an important role in war.
A map excerpt caused a stir on Twitter, which allegedly shows where Russian soldiers with their country's SIM cards are registered in the Ukrainian mobile network. Where the troop concentration is particularly high, the map glows yellow to red. Among other things, the Ukrainian military could see exactly where Russia is assembling units to prepare attacks and thus prepare the defense.
However, the origin of the card is questionable and has some inconsistencies. Among other things, the red and yellow areas do not match the current combat zones. But this can probably be explained relatively easily: the original post says that the map probably shows the situation in March.
In principle, it is possible for operators of a mobile network to determine their positions based on the base stations to which smartphones register. They can also determine whether it is a foreign SIM card. However, a Twitter user refers to the message from a friend who works at the Ukrainian mobile operator Kyivstar. He writes that in the areas occupied by Russia, the Ukrainian stations have been destroyed or disconnected, so local mobile phone providers no longer have such data. The card must therefore be a fake.
In addition, according to the Ukrainian "Pravda", Ukrainian providers blocked their networks for Russian and Belarusian SIM cards immediately after the start of the invasion. This is also one of the reasons why Russian soldiers took their smartphones from Ukrainians and forced them to hand over their device and SIM PINs.
This in turn made it possible in many cases to determine the positions of looters. Because both iPhones and Android smartphones have the option of locating stolen or lost devices. There is also the option to block smartphones, but in this case this is only advisable after the occupiers have left.
Many Russian soldiers are said to be using Ukrainian SIM cards in their smartphones, often from dubious sources. This makes it easy for Ukrainians to eavesdrop on them, especially if they sold them the tickets themselves.
Another type of smartphone tracking is extremely relevant for the military, and it doesn't matter whether a SIM card is blocked. Because for them it is enough that the devices try to contact a mobile antenna.
This circumstance is used by accommodating receivers in drones or vehicles that simulate transmission masts (cell site simulators). If a smartphone connects to such a decoy, attackers may be able to access GPS data or other information directly.
The simulator can also determine the distance to a smartphone based on the strength of the signal. If this happens from several directions, the approximate location can be determined. It is also possible that decoys determine the position of a smartphone by retrieving the signal strengths of various real cell towers in the vicinity of a smartphone.
According to "Sky News", it is known that the Russians are using the Leer-3 electronic warfare system, which consists of a command truck and two aerial drones (Orlan-10). It is also capable of disrupting enemy networks.
According to "Inform Napalm", Leer-3 was spotted in occupied Donetsk in 2015. The system should be able to receive more than 2,000 telephones within a radius of six kilometers. It is assumed that the Ukrainian army uses a similar technology, according to "Sky News".
Because of the smartphone problem, the Ukrainian army had already issued corresponding instructions for soldiers deployed against Russian-led separatists in the Donbass before the February 24 invasion. Among other things, they should not use their own SIM card, but buy one locally. When making phone calls, they should move far away from the troops and, if possible, go to towns with many civilians. Otherwise, you should always leave your phone switched off.
However, John Scott Railton of the University of Toronto told Sky News that attackers could also use drone access to hack a smartphone so that it appears turned off but is actually a beacon on the battlefield. Removing the battery is one solution, but this is practically impossible with current smartphones.
Given the threat posed by smartphones in the field, one wonders why the Russian army didn't attack Ukraine's cellular networks completely. Sam Cranny-Evans of defense think tank RUSI told Sky News that destroying a cell-dense mobile network is not easy. Even in Mariupol there was still reception after weeks of fighting.
The Russians may also need the Ukrainian mobile network themselves. Their communication problems are well known, apparently they don't even have enough digital military radios. According to Christo Grozev from the research platform "Bellingcat", they actually paralyzed the network in Kharkiv at the beginning of March, which also made it impossible to use their Era cryptophones, which are dependent on existing 3G/4G networks.
This circumstance may have led to the death of Major General Vitali Gerasimov. According to leaked recordings of a wiretapped conversation between two Russian officers about the general's death released by the Ukrainian secret service, Era was not working. According to Grozev, the officers used Ukrainian SIM cards.
To prevent further losses from the use of smartphones, President Putin signed a decree on May 6th. According to Radio Free Europe, it states that military personnel should not own devices that can determine locations and transmit audio and photo material. Violation of the rule is considered a gross disciplinary offence.
6